| CPC H04L 63/1483 (2013.01) [G06F 11/00 (2013.01); G06F 21/40 (2013.01); G06F 21/43 (2013.01); G06F 21/44 (2013.01); G06F 21/45 (2013.01); G06F 21/554 (2013.01); G06F 21/566 (2013.01); G06F 21/57 (2013.01); G06F 21/64 (2013.01); H04L 9/3213 (2013.01); H04L 41/0631 (2013.01); H04L 41/142 (2013.01); H04L 43/10 (2013.01); H04L 51/212 (2022.05); H04L 63/02 (2013.01); H04L 63/0209 (2013.01); H04L 63/0227 (2013.01); H04L 63/0236 (2013.01); H04L 63/0254 (2013.01); H04L 63/0428 (2013.01); H04L 63/08 (2013.01); H04L 63/0807 (2013.01); H04L 63/10 (2013.01); H04L 63/14 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 63/1466 (2013.01); H04L 63/1491 (2013.01); H04L 63/164 (2013.01); H04L 63/20 (2013.01); H04L 67/104 (2013.01)] | 20 Claims |
|
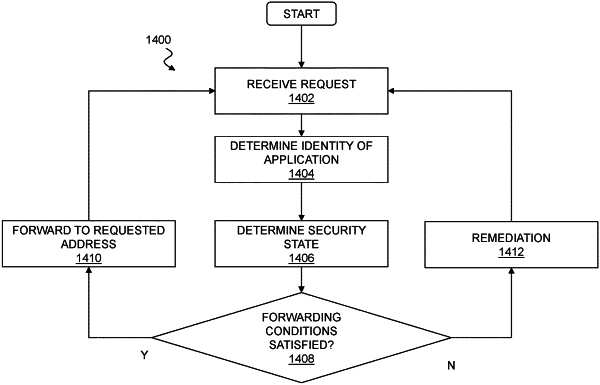
1. A computer program product for operating a firewall to selectively forward network communications between a first network interface of the firewall operable to couple to an endpoint and a second network interface of the firewall operable to couple to a remote resource hosted at a server, the computer program product comprising computer executable code embodied in a non-transitory memory of the firewall that, when executing on the firewall, responds to a request from the endpoint to the remote resource by performing the steps of:
detecting indicia of maliciousness in the request;
in response to the indicia, determining an identity of an application that originated the request on the endpoint based on a packet carrying the request;
determining a security state of the application that originated the request by querying a security data recorder on the endpoint to identify previous events associated with the application; and
conditionally forwarding the request from the firewall to the server only when the identity of the application is recognized and the security state of the application is uncompromised.
|