| CPC H04L 63/1483 (2013.01) [G06N 20/00 (2019.01); H04L 63/08 (2013.01); H04L 63/10 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
1. A computer system for automated interaction with malicious computing agents, the computer system comprising:
a processor coupled to computer memory and non-transitory computer readable media, the processor configured to:
generate a set of one or more bait confidential user credentials corresponding to a simulated user;
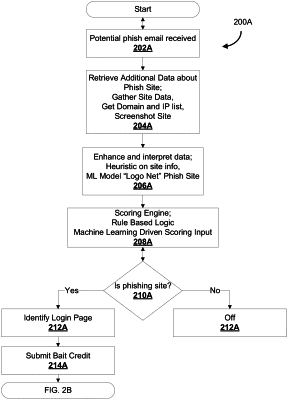
load a malicious online resource that is configured to fraudulently obtain one or more confidential user credentials and identify one or more input fields in the malicious online resource;
automatically traverse one or more webpages of the malicious online resource and insert the one or more bait confidential user credentials into the one or more input fields of the malicious online resource;
receive, in a new session on a production instance of a secure online resource, a new set of user credentials requesting access to the secure online resource;
responsive to the new set of user credentials including at least one user credential matching the one or more bait confidential user credentials corresponding to the simulated user, flag the new session as a malicious actor session;
route the malicious actor session to a sandbox instance of the secure online resource where one or more characteristics of interactions with the sandbox instance are recorded into a malicious interaction fingerprint dataset;
generate, during one or more unclassified sessions of the secure online resource, corresponding one or more unclassified interaction fingerprint datasets, the one or more unclassified interaction fingerprint datasets each representative of recorded characteristics of interactions;
determine, for each of the one or more unclassified sessions, a corresponding malicious actor similarity data value by comparing each of the one or more unclassified interaction fingerprint datasets against the malicious interaction fingerprint dataset;
retrieve, for each of the one or more unclassified sessions, a baseline user profile fingerprint dataset trained based at least on a corpus of prior interactions by a user;
determine, for each of the one or more unclassified sessions, a corresponding baseline similarity data value by comparing each of the one or more unclassified interaction fingerprint datasets against the baseline user profile fingerprint fingerprint dataset; and
classify one or more sessions of the one or more unclassified sessions as a suspicious session based upon a weighted combination of the corresponding baseline similarity data value and the corresponding malicious actor similarity data value.
|