| CPC H04L 63/1433 (2013.01) [H04L 63/20 (2013.01)] | 18 Claims |
|
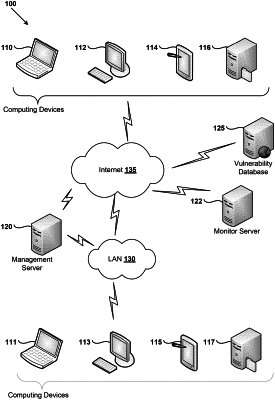
1. A method of vulnerability paring for scanning a target computer, the method comprising:
receiving a plurality of ordered patch milestones, each of the patch milestones designating a set of one or more vulnerability scanning rules having an associated scanning order;
based on a current patch level for the target computer, selecting a set of one or more of but not all of the patch milestones, wherein at least some of the patch milestones are not selected based on the ordering of the patch milestones and the current patch level, wherein the ordering of the patch milestones defines whether an install date of a first patch milestone of the plurality of ordered patch milestones precedes or supercedes an install date a second patch milestone of the plurality of ordered patch milestones; and
evaluating the selected set of patch milestones, the evaluating comprising executing at least one of the vulnerability scanning rules associated with the selected set of patch milestones.
|