| CPC H04L 63/105 (2013.01) [H04L 41/14 (2013.01); H04L 63/1425 (2013.01); H04L 63/1483 (2013.01)] | 18 Claims |
|
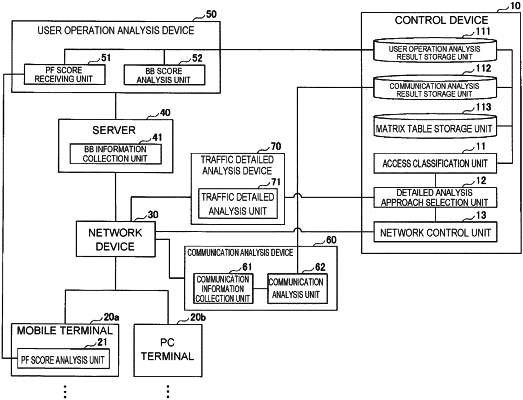
1. An access analysis system comprising one or more processors and a memory configured to:
detect one or more requests from a terminal to access a server over a network;
analyze a first characteristic of the one or more requests;
based on the analyzed first characteristic of the one or more requests, determine a first score indicative of a validity of a user at the terminal that transmitted the one or more requests to the server;
analyze a second characteristic of the one or more requests;
based on the analyzed second characteristic, determine data indicative of a normality of the one or more requests;
in response, generate a second score based on (i) the first score and (ii) the data indicative of the normality of the one or more requests, the second score indicative of a classification of the validity of the terminal's access to the server, wherein the second score is generated by applying, to a matrix table, (i) the first score indicative of the validity of the user at the terminal that transmitted the one or more requests and (ii) the data indicative of the normality of the one or more requests, the matrix table showing validity of access via the network according to a combination of i) a level at which the user is valid and ii) a level at which the communication is normal; and
in response to analyzing the second score, transmit a notification to a device that monitors communications with the server over the network, the notification indicating that the one or more requests from the terminal (i) are unauthorized and (ii) to block subsequent requests transmitted by the terminal to the server over the network.
|