| CPC H04L 63/10 (2013.01) [G06F 21/606 (2013.01); G06F 21/6218 (2013.01); H04L 67/1097 (2013.01); H04L 67/12 (2013.01); G06F 2221/2141 (2013.01); H04L 2209/60 (2013.01)] | 10 Claims |
|
1. A data access processing method for an industrial Internet cloud service platform, comprising:
step 1, transmitting, by an industrial device with data to be accessed, a data access request to a data processing unit of the platform, and meanwhile uploading a device identifier capable of identifying the industrial device with data to be accessed;
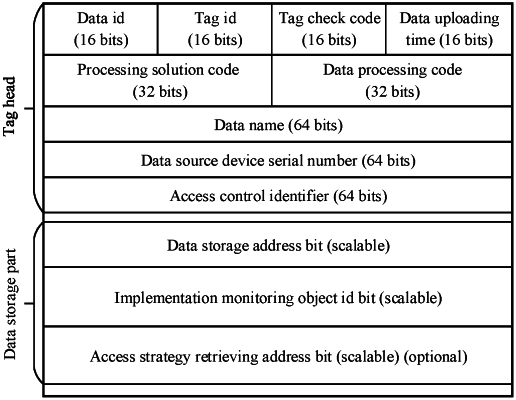
step 2, retrieving, by the data processing unit, a data upload authentication tag matching the data to be accessed from a traceability unit according to the data access request; under the condition that the data upload authentication tag is successfully retrieved, proceeding to step 3; otherwise, rejecting, by the data processing unit, a current data access request of the industrial device with data to be accessed, and then completing current data access processing;
step 3, determining, by the data processing unit, validity of the data upload authentication tag according to a tag check code in the data upload authentication tag; under the condition that the data upload authentication tag is valid, proceeding to step 4; otherwise, rejecting, by the data processing unit, the current data access request of the industrial device with data to be accessed, meanwhile, deleting the data upload authentication tag from the traceability unit, and then completing the current data access processing;
step 4, obtaining, by the data processing unit, a data processing code and an access control identifier of the data to be accessed from the data upload authentication tag; under the condition that the data processing code is NRP and the access control identifier is NULL or GEN, proceeding to step 5; otherwise, proceeding to step 7;
step 5, under the condition that the access control identifier is GEN, proceeding to step 6; otherwise, directly accessing, by the industrial device with data to be accessed, the data to be accessed according to a data storage address in the data upload authentication tag, and then completing the current data access processing;
step 6, obtaining, by the data processing unit, an access strategy for the data to be accessed from an access strategy retrieving address bit of the data upload authentication tag, then operating an attribute-based access control function, and determining whether the industrial device with data to be accessed has authority to access the data to be accessed according to the access strategy; under the condition that the industrial device with data to be accessed has access authority, accessing, by the industrial device with data to be accessed, the data to be accessed according to the access authority and the data storage address of the data to be accessed, and completing the current data access processing; otherwise, rejecting, by the data processing unit, the current data access request of the industrial device with data to be accessed, and then completing the current data access processing;
step 7, recommending, by a sensor network of the platform, an optimal data access processing solution suitable for the industrial device with data to be accessed to the data processing unit according to the device identifier, the data upload authentication tag, and a current actual operation condition of the platform;
step 8, determining, by the data processing unit, an implementation monitoring object for monitoring implementation of a current data access processing task according to the optimal data access processing solution; under the condition that the implementation monitoring object is the data processing unit, proceeding to step 9; otherwise, proceeding to step 11;
step 9, assisting, by the data processing unit, the industrial device with data to be accessed to install a secure communication algorithm according to the optimal data access processing solution, and after installation is completed, establishing a temporary secure channel of the industrial device with data to be accessed according to the algorithm;
step 10, obtaining, by the data processing unit, the data to be accessed and the access strategy from a storage unit of the platform and an access control module of the data processing unit according to a data storage address bit and the access strategy retrieving address bit of the data upload authentication tag, respectively; then decrypting, by the data processing unit, the data to be accessed according to the optimal data access processing solution and the access strategy; under the condition that decryption of the data to be accessed fails, determining that the industrial device with data to be accessed has no access authority, rejecting, by the data processing unit, the current data access request of the industrial device with data to be accessed, closing the temporary secure channel, and then completing the current data access processing; otherwise, transmitting, by the data processing unit, decrypted data to the industrial device with data to be accessed via the temporary secure channel, closing the temporary secure channel, and then completing the current data access processing;
step 11, under the condition that the implementation monitoring object is the industrial device with data to be accessed, proceeding to step 12; otherwise, proceeding to step 15;
step 12, assisting, by the data processing unit, the industrial device with data to be accessed to install the secure communication algorithm according to the optimal data access processing solution, and after installation is completed, establishing the temporary secure channel of the industrial device with data to be accessed according to the algorithm;
step 13, based on the optimal data access processing solution, assisting, by the data processing unit, the industrial device with data to be accessed to install a decryption facility suitable for the data to be accessed by means of the temporary secure channel; and then obtaining, by the data processing unit, the data to be accessed and the access strategy from the storage unit and the access control module of the data processing unit according to the data storage address bit and the access strategy retrieving address bit of the data upload authentication tag, respectively, and then transmitting the data to be accessed and the access strategy to the industrial device with data to be accessed via the temporary secure channel;
step 14, decrypting, by the industrial device with data to be accessed, the data to be accessed by means of the decryption facility; under the condition that the industrial device with data to be accessed successfully decrypts the data to be accessed, determining, by the data processing unit, that the industrial device with data to be accessed successfully accesses data, closing the temporary secure channel, and then completing the current data access processing; otherwise, determining that the industrial device with data to be accessed has no access authority, meanwhile, rejecting, by the data processing unit, the current data access request of the industrial device with data to be accessed, closing the temporary secure channel, and then completing the current data access processing;
step 15, selecting, by the data processing unit, qualified devices to form a cooperative computing device group according to the optimal data access processing solution and a specific condition of the industrial device in a device terminal candidate pool; and after the cooperative computing device group is successfully formed, assisting, by the data processing unit, the cooperative computing device group and the industrial device with data to be accessed to install the secure communication algorithm according to an optimal data processing solution, and after installation is completed, establishing the temporary secure channel of the cooperative computing device group and the industrial device with data to be accessed according to the algorithm;
step 16, based on the optimal data access processing solution, assisting, by the data processing unit, the cooperative computing device group to install the decryption facility suitable for the data to be accessed by means of the temporary secure channel; and then obtaining, by the data processing unit, the data to be accessed and the access strategy from the storage unit and the access control module of the data processing unit according to the data storage address bit and the access strategy retrieving address bit of the data upload authentication tag, respectively, and then transmitting the data to be accessed and the access strategy to the cooperative computing device group via the temporary secure channel; and
step 17, decrypting, by the cooperative computing device group, the data to be accessed by means of the decryption facility according to the access strategy; under the condition that the cooperative computing device group successfully decrypts the data to be accessed, transmitting, by the cooperative computing device group, the decrypted data to the industrial device with data to be accessed via the temporary secure channel, specifically, determining, by the data processing unit, that the industrial device with data to be accessed successfully accesses data, closing the temporary secure channel, dismissing the cooperative computing device group, and then completing the current data access processing; otherwise, determining that the industrial device with data to be accessed has no access authority, specifically, rejecting, by the data processing unit, the current data access request of the industrial device with data to be accessed, closing the temporary secure channel, dismissing the cooperative computing device group, and then completing the current data access processing.
|