| CPC H04L 63/0861 (2013.01) [G06F 21/316 (2013.01); G06F 21/32 (2013.01); G10L 15/26 (2013.01); G10L 17/14 (2013.01); G10L 17/26 (2013.01)] | 18 Claims |
|
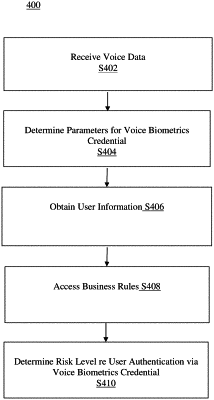
1. A method for determining whether a voice biometrics credential provides a reliable mechanism for authenticating a user, the method comprising:
detecting an event over a network that includes a requested function comprising a voice request from a user to perform the function;
extracting event header data and event detail data;
determining that the user must be authenticated before performing the requested function;
determining a first authentication factor of a plurality possible authentication factors by selecting a default authentication factor from a selection of authentication factors comprising only a voice biometric authentication factor;
in response to determining the first authentication factor, prompting the user to provide at least one set of voice data comprising a user-specific voice biometrics credential before determining whether additional authentication credentials from the plurality of possible authentication factors is required from the user;
in response to the prompt, receiving spoken words from the user;
determining, based only on the received spoken words, a value of at least one parameter including one or more audio characteristics that corresponds to the user-specific voice biometrics credential;
determining a level of authentication of the user based on the determined value;
obtaining at least one user-specific item of information;
combining the user-specific item of information with the event header data and the event detail data for providing enrichment data;
accessing at least one business rule that relates to the user and the requested function;
determining a risk level of the requested function based on the at least one business rule;
based on the determined risk level, evaluating a combination of the at least one set of voice data, the at least one user-specific item of information, and the at least one business rule for selecting a best credential for authenticating the user;
determining, based on the at least one set of voice data, the at least one user-specific item of information, and the at least one business rule, whether the user-specific voice biometrics credential is the best credential for authenticating the user;
determining whether the level of authentication is sufficient to authenticate the user for the requested function based on the determined risk level;
authenticating the user using the determined value without requesting additional information from the user when the level of authentication is determined to be sufficient for authentication for the determined risk level associated with the requested function, and based on the requested function, the at least one set of voice data, the at least one user-specific item of information, and the at least one business rule;
requesting, from the user, the additional authentication credentials when the level of authentication is determined to be insufficient for authentication for the determined risk level associated with the requested function;
authenticating the user using the additional authentication credentials instead of the determined value when the level of authentication is determined to be insufficient for authentication for the determined risk level associated with the requested function, and based on the requested function, the at least one set of voice data, the at least one user-specific item of information, and the at least one business rule
and in response to authenticating the user using either the determined value or using the additional authentication credentials, performing the function.
|