| CPC H04L 63/0853 (2013.01) [G06F 16/2379 (2019.01)] | 20 Claims |
|
1. A computer system, comprising:
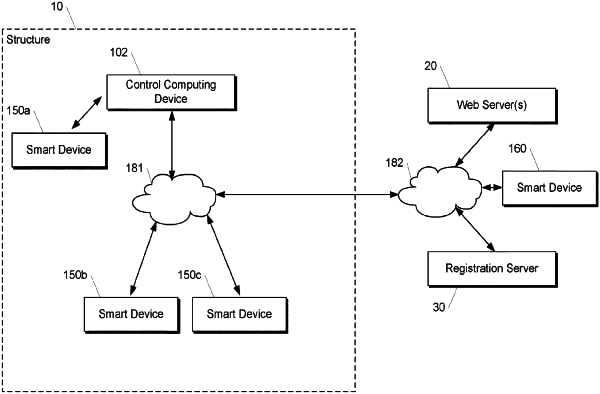
a control computing device physically located within a physical structure, and wherein the control computing device comprises one or more processors and one or more non-transitory computer-readable media that store instructions that, when executed by the one or more processors, cause the control computing device to perform operations, the operations comprising:
receiving, from a first user, a first set of user credentials for one or more of: a first computing device physically located within the physical structure, a first application, or a first web service;
receiving a structure identifier assigned to the physical structure;
assigning the first set of user credentials to the structure identifier to generate a first set of structure credentials that are distinct from the first set of user credentials, wherein the first set of structure credentials enables one or more authorized users, distinct from the first user, to access the one or more of the first computing device, the first application, or the first web service;
receiving, from a second user, a request to control the one or more of the first computing device, the first application, or the first web service;
in response to receiving the request from the second user, determining whether the second user is one of the one or more authorized users; and
in response to determining that the second user is one of the one or more authorized users, using the first set of structure credentials to enable the second user to access the one or more of the first computing device, the first application, or the first web service.
|