| CPC H04L 63/0853 (2013.01) | 20 Claims |
|
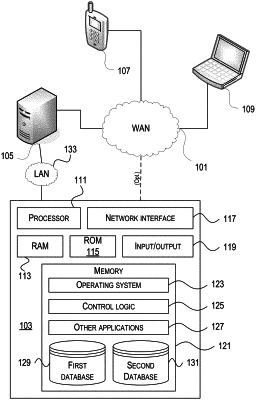
1. A system comprising:
a first identity provider application executing on a first computing device; and
a second identity provider application executing on a second computing device;
wherein the first identity provider application is configured to:
receive an indication of an authentication request;
retrieve, from a storage device, session information associated with the authentication request;
receive, from a third computing device, authentication credentials;
authenticate, based on the session information, based on the authentication credentials, and by performing one or more first functions of a first authentication protocol, a user; and
modify, in response to the authenticating, the session information to store an identification of the one or more first functions of the first authentication protocol used to authenticate the user; and
wherein the second identity provider application is configured to:
determine a first level of security based on the identification of the one or more first functions of the first authentication protocol stored in the session information;
determine a plurality of second functions of a different authentication protocol for authenticating the user;
determine a second level of security based on the plurality of second functions;
determine, based on the difference between the one or more first functions of the first authentication protocol and the plurality of second functions, wherein the first level of security is different from the second level of security, and based on determining that at least a portion of the one or more first functions of the first authentication protocol satisfy the second level of security associated with the different authentication protocol, a subset of the plurality of second functions of the different authentication protocol for authenticating the user; and
authenticate, based on the modified session information and by performing the subset of the plurality of second functions, the user.
|