| CPC H04L 63/083 (2013.01) [H04L 63/0853 (2013.01); H04L 63/0861 (2013.01); H04L 63/107 (2013.01); H04W 4/023 (2013.01); H04W 12/065 (2021.01); H04W 12/08 (2013.01); H04L 2463/082 (2013.01)] | 20 Claims |
|
1. A system for facilitating authentication based on a dynamic distance threshold, comprising:
a computer system comprising one or more physical processors programmed with computer program instructions that, when executed, cause operations comprising:
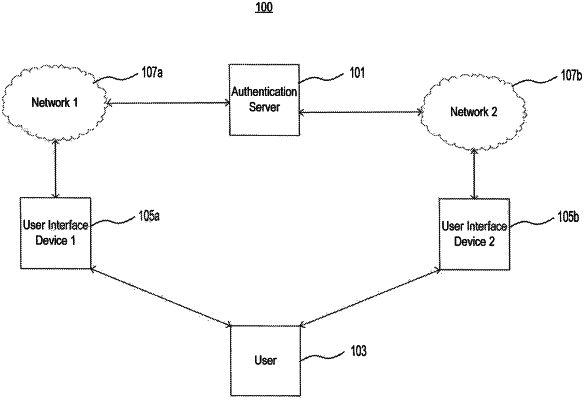
receiving an authentication request from a first user device associated with a user;
obtaining first location information of the first user device and second location information of a second user device;
determining a distance between the first user device and the second user device based on the first and second location information;
adjusting a distance threshold based on (i) whether the first and second location information are obtained over a same wireless network, (ii) whether the first or second location information is obtained over a public wireless network, or (iii) whether an IP address from which the first or second location information is obtained matches a stored IP address;
subsequent to the adjustment, comparing the distance to the distance threshold; and
authenticating the user based on a result of the comparison.
|