| CPC H04L 63/083 (2013.01) [H04L 9/3263 (2013.01); H04L 63/0492 (2013.01); H04L 63/061 (2013.01)] | 19 Claims |
|
1. A security key device, comprising:
a physical interface adapted to plug into an electronic device;
a communication module;
a security processing unit, configured to execute programs of an authentication module, a bridge module, and a management module, wherein the programs of the authentication module, the bridge module, and the management module are stored in the security key device;
a processing unit, coupled to the communication module and the security processing unit; and
a confirmation unit coupled to the processing unit,
wherein the authentication module is configured to operate according to a Fast IDentity Online protocol, and the management module is configured to operate according to a Public Key Infrastructure (PKI) protocol, and the management module is further configured to store key data which are generated by the management module according to the Public Key Infrastructure protocol,
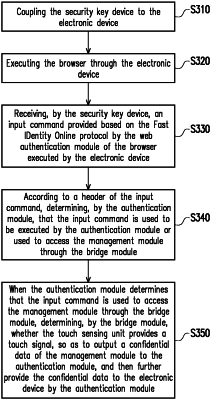
wherein the authentication module receives an input command through the communication module, the input command is provided by a web authentication module of a browser executed by the electronic device based on the Fast IDentity Online protocol, and the authentication module determines that the input command is used to be executed by the authentication module or used to access the management module through the bridge module according to a header of the input command, so that the management module outputs the key data to the authentication module,
wherein when the authentication module determines that the input command is used to access the management module through the bridge module, the bridge module determines whether the confirmation unit provides a confirmation signal, so as to output a confidential data of the management module to the authentication module, and then further provide the confidential data to the electronic device by the authentication module, wherein the confidential data is generated based on the PKI protocol.
|