| CPC H04L 63/08 (2013.01) [G06F 21/602 (2013.01); H04L 9/0816 (2013.01); H04L 9/0844 (2013.01); H04L 9/3271 (2013.01); H04L 63/0428 (2013.01); H04L 63/06 (2013.01); H04L 63/0853 (2013.01); H04L 63/0869 (2013.01); H04W 12/041 (2021.01); H04W 12/0431 (2021.01); H04W 12/069 (2021.01); H04W 12/10 (2013.01); H04L 63/123 (2013.01); H04L 2463/082 (2013.01)] | 19 Claims |
|
1. A first network device of a first communication network, the first network device comprising:
processing circuitry; and
memory coupled with the processing circuitry, wherein the memory includes instructions that when executed by the processing circuitry causes the first network device to perform operations comprising:
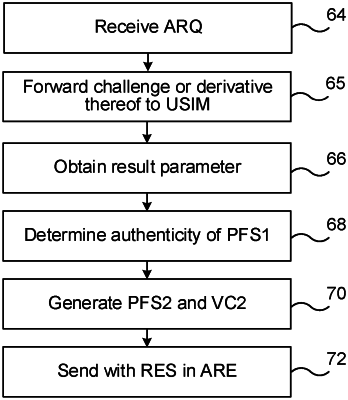
obtaining a challenge;
obtaining a first Diffie-Hellman (DH) parameter;
obtaining a first verification code for the first DH parameter;
sending, by the first network device, the challenge, the first DH parameter, and the first verification code to a communication device;
receiving, at the first network device, a second DH parameter, a second verification code, and a response parameter from the communication device;
determining that the response parameter is authentic;
verifying the second DH parameter based on the second verification code;
computing a session key for communication between the communication device and the first network device, the session key being based on the first DH parameter and the second DH parameter; and
transmitting messages towards the communication device using the session key to provide perfect forward security.
|