| CPC H04L 63/0435 (2013.01) [G06F 21/6218 (2013.01); H04L 9/3242 (2013.01)] | 20 Claims |
|
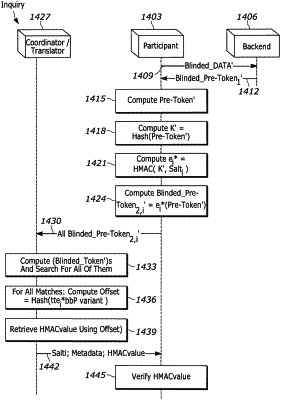
1. A method for data corroboration via tokenization, as a process resulting in at least one token, invoking a protocol jointly managed by a first control circuit configured as a first network element and a second control circuit configured as a second network element, the method comprising:
the first network element provisioned with a first set of tokens representing a first set of entities;
the second network element provisioned with a second set of tokens representing a second set of entities;
establishment between the first network element and the second network element of at least one key;
transmission by the first network element to the second network element of a first message comprised, at least in part, of a first set of transformed tokens derived by transforming, as a first transformation process, using a first key of the at least one key each token of a first subset of tokens as a subset of the first set of tokens; and
comparison by the second network element of at least one of the transformed tokens of the first message to at least one transformed token of a second set of transformed tokens derived by transforming, as a second transformation process, using the first key a second subset of tokens as a subset of the second set of tokens.
|