| CPC G06Q 10/0635 (2013.01) [G06F 9/542 (2013.01); G06F 11/079 (2013.01); G06F 16/955 (2019.01); G06F 17/18 (2013.01); G06F 18/214 (2023.01); G06F 18/2178 (2023.01); G06F 18/23213 (2023.01); G06F 18/24143 (2023.01); G06F 21/554 (2013.01); G06F 21/56 (2013.01); G06F 21/562 (2013.01); G06F 21/565 (2013.01); G06N 5/01 (2023.01); G06N 5/022 (2013.01); G06N 5/04 (2013.01); G06N 5/046 (2013.01); G06N 7/00 (2013.01); G06N 20/00 (2019.01); G06N 20/20 (2019.01); G06Q 10/06395 (2013.01); G06V 20/52 (2022.01); H04L 63/0227 (2013.01); H04L 63/0263 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); G06Q 30/0185 (2013.01); G06Q 30/0283 (2013.01)] | 20 Claims |
|
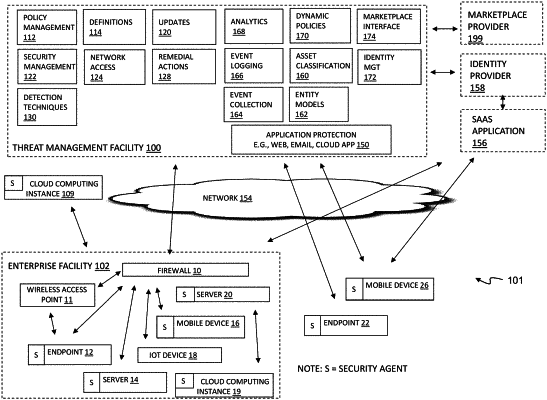
1. A system comprising:
a local agent executing on an endpoint coupled to an enterprise network;
a data recorder executing on the endpoint that stores locally on the endpoint an unfiltered event stream of event data for changes occurring to computing objects on the endpoint, the local agent executing a filter on the endpoint for creating a filtered event stream with a subset of event data for changes detected on the endpoint from the unfiltered event stream captured by the data recorder;
a query interface on the endpoint for receiving queries to the data recorder from a remote resource;
a local security agent executing on the endpoint, the local security agent configured to detect malware on the endpoint based on event data stored by the data recorder, and further configured to communicate the filtered event stream over the enterprise network; and
a threat management facility coupled in a communicating relationship with the enterprise network, the threat management facility configured to receive the filtered event stream from the local security agent, detect malware on the endpoint based on the filtered event stream, and remediate the endpoint when malware is detected by communicating with the local security agent executing on the endpoint, the threat management facility further configured to modify security functions within the enterprise network based on a security state of the endpoint.
|