| CPC G06N 3/126 (2013.01) [G06F 21/577 (2013.01); G06N 5/02 (2013.01); G06F 2221/034 (2013.01)] | 17 Claims |
|
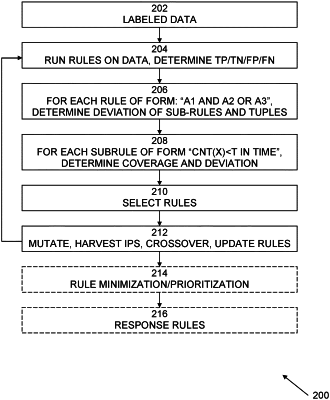
1. A method, implemented in a computer comprising a processor, memory accessible by the processor, and computer program instructions stored in the memory and executable by the processor, the method comprising:
simulating operation of a security incident and event management system by running a plurality of rules of the system on labeled data;
determining fitness metrics of the plurality of rules, wherein the fitness metrics include:
a standard deviation of values of each sub-rule and of each tuple of sub-rules from a mean of the values of each of the sub-rules and each tuple of the sub-rules per a simulation period for a first rule of the plurality of rules;
an additional coverage of events associated with the first rule of the plurality of rules; and
a reciprocal of a number of data fields used in the first rule of the plurality of rules;
selecting at least one rule of the plurality of rules based on the determined fitness metrics;
modifying the selected rule to form an updated rule; and
repeatedly running the updated rule on the labeled data, determining fitness metrics of the updated rule, and mutating the updated rule until reaching one of a predetermined level of fake positive rate-true positive rate (FPR-TPR), a timeout, or a maximum number of repetitions.
|