| CPC G06F 21/78 (2013.01) [G06F 3/0604 (2013.01); G06F 3/067 (2013.01); G06F 3/0622 (2013.01); G06F 3/0653 (2013.01); G06F 3/0659 (2013.01); G06F 21/566 (2013.01); G06F 21/577 (2013.01)] | 19 Claims |
|
1. A method comprising:
determining, by a data protection system, that a total amount of read traffic and write traffic processed by a storage system during a time period exceeds a threshold;
determining, by the data protection system, a first compressibility metric associated with the write traffic, the first compressibility metric indicating an amount of storage space saved if the write traffic is compressed;
determining, by the data protection system, a second compressibility metric associated with the read traffic, the second compressibility metric indicating an amount of storage space saved if the read traffic is compressed;
determining, by the data protection system based on a comparison of the first compressibility metric with the second compressibility metric, that the write traffic is less compressible than the read traffic;
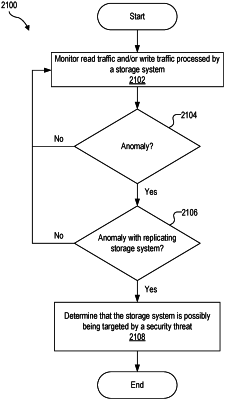
identifying, by the data protection system, an anomaly in a relationship between one or more input operations and one or more output operations performed between a source and the storage system; and
determining, by the data protection system based on the identifying of the anomaly and based on the total amount of read traffic and write traffic exceeding the threshold and based on the write traffic being less compressible than the read traffic, that the storage system is possibly being targeted by a security threat.
|