| CPC G06F 21/6254 (2013.01) [G06F 21/6263 (2013.01); G06N 5/04 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
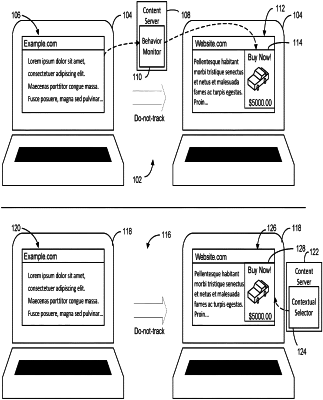
1. A method for detecting third-party re-identification of anonymized computing devices, comprising:
receiving, by a client device, a plurality of first content items within a predetermined time period;
subsequently transmitting, by the client device, a first request for a content item from a content provider;
receiving, by the client device, a second content item from the content provider in response to the first request; and
transmitting, by the client device, a second request for a content item from the content provider, the second request blocked by an intermediary server responsive to the intermediary server determining that a signal or a combination of signals with a highest predictive ability between a first set of identifications of third content items retrieved by a first anonymized computing device and a second set of identifications of fourth content items retrieved by a second anonymized computing device exceeds a threshold, the third content items and the fourth content items retrieved prior to the respective first or second anonymized computing devices receiving the second content item.
|