| CPC G06F 21/6218 (2013.01) [G06F 16/176 (2019.01); G06F 16/1734 (2019.01); G06F 21/52 (2013.01)] | 20 Claims |
|
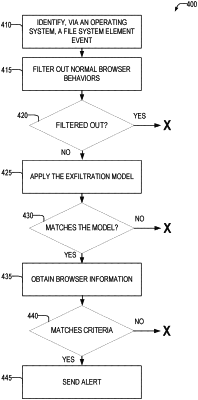
1. A method for detecting file exfiltration, the method comprising:
using one or more processors, executing an exfiltration detection application, the exfiltration detection application performing operations comprising:
identifying a file system element event using an operating system interface;
determining that the file system element event corresponds to a web-browser application, the web-browser application a separate application from the exfiltration detection application;
responsive to determining that the file system element event corresponds to the web-browser application, determining whether the file system element event matches an exfiltration signature model that considers one or more characteristics of the file system element event or a second file system element event;
responsive to determining that the file system element event matches the exfiltration signature model, determining a website visited by the web-browser application corresponding to the file system element event;
determining, based upon the website visited, whether to send an alert to an administrative computing device; and
responsive to determining that an alert is to be sent, sending the alert to the administrative computing device, the alert indicating that a file system element event that is characteristic of an unauthorized file exfiltration has been detected.
|