| CPC G06F 21/577 (2013.01) [G06F 3/0484 (2013.01); G06F 16/252 (2019.01); G06F 2221/033 (2013.01); G06Q 10/0635 (2013.01)] | 20 Claims |
|
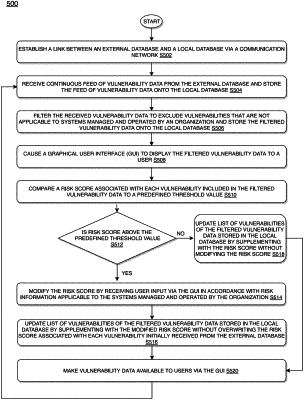
1. A method for managing vulnerability data by utilizing one or more processors and one or more memories, the method comprising:
establishing a link between an external database external to a vulnerability data management device managed and operated by an organization and a local database embedded within the vulnerability data management device via a communication network;
receiving continuous feed of vulnerability data from an external database and storing the feed of vulnerability data onto a local database, the vulnerability data including a list of vulnerabilities and corresponding risks;
filtering the received vulnerability data to exclude vulnerabilities that are not applicable to systems managed and operated by the organization and storing the filtered vulnerability data onto the local database;
causing a graphical user interface (GUI) to display the filtered vulnerability data to a user;
comparing a risk score associated with each vulnerability included in the filtered vulnerability data to a predefined threshold value;
determining, based on comparing, whether the risk score exceeds the predefined threshold value;
modifying, based on determining that the risk score exceeds the predefined threshold value, the risk score by receiving user input via the GUI in accordance with risk information applicable to the systems managed and operated by the organization;
updating the list of vulnerabilities of the filtered vulnerability data stored in the local database by supplementing with the modified risk score without overwriting the risk score associated with each vulnerability initially received from the external database;
creating a first queue in the local database for vulnerabilities with risk scores that have been received from the external database;
creating a second queue for vulnerabilities with risk scores that have been modified by the user; and
causing the GUI to display the first queue and the second queue in a manner such that a reviewer is not allowed to modify the second queue.
|