| CPC G06F 21/566 (2013.01) [G06F 16/2246 (2019.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
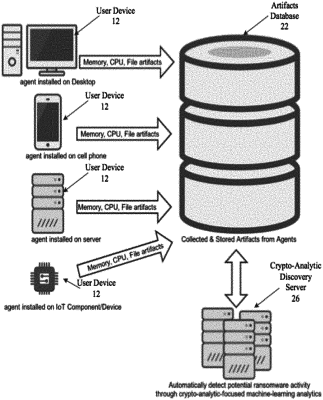
1. A method for protecting a computing device of a target system against ransomware attacks, wherein the computing device employs a file system having a data structure used by an operating system of the computing device for accessing files based on file paths, wherein operating system uses a filing system implemented in a storage having a directory that contains a list of file names and other information related to the files, including the file paths, the method comprising the steps of:
a. installing an agent in the computing device, wherein the agent is a software or a hardware that performs one or more actions autonomously on behalf of the target system, including specifying one or more saved file paths in the storage device to one or more trap files each having a trap file name in the directory, wherein a trap file is a file access to which indicates a probability of ransomware attack;
b. monitoring access to the one or more trap files to detect the probability of ransomware attack;
c. upon detecting access to a trap file, performing a remedial action against the probability of ransomware attack.
|