| CPC G06F 21/554 (2013.01) [G06F 21/566 (2013.01); G06F 2221/034 (2013.01)] | 21 Claims |
|
1. A system, comprising:
a processor configured to:
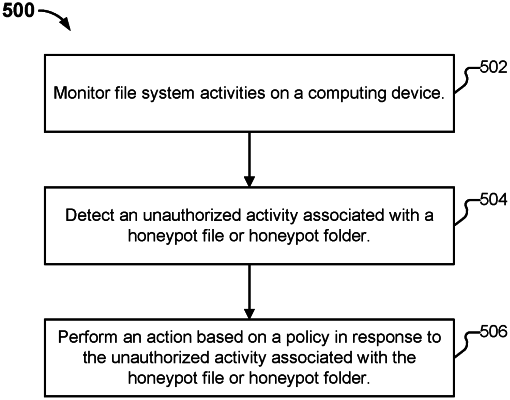
monitor file system activities on a computing device;
detect an unauthorized activity associated with a honeypot file or honeypot folder, wherein the honeypot file is a virtual file generated as a spoofed file system response using a filter driver or the honeypot folder is a virtual folder generated as the spoofed file system response using the filter driver, wherein the virtual file is dynamically generated using the filter driver with at least one of the following: a spoofed header, a spoofed time stamp, and a spoofed file size; and
perform an action based on a policy in response to the unauthorized activity associated with the honeypot file or the honeypot folder, wherein the action comprises one or more of the following: kill a process based on the policy in response to the unauthorized activity associated with the honeypot file or the honeypot folder associated with the process, or generate an alert based on the policy in response to the unauthorized activity associated with the honeypot file or honeypot folder; and
a memory coupled to the processor and configured to provide the processor with instructions.
|