| CPC G06F 21/34 (2013.01) [G06F 21/335 (2013.01); G06F 21/602 (2013.01); G06F 21/604 (2013.01); H04L 63/0428 (2013.01); H04L 63/0853 (2013.01); G06F 2221/2137 (2013.01); G06F 2221/2153 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
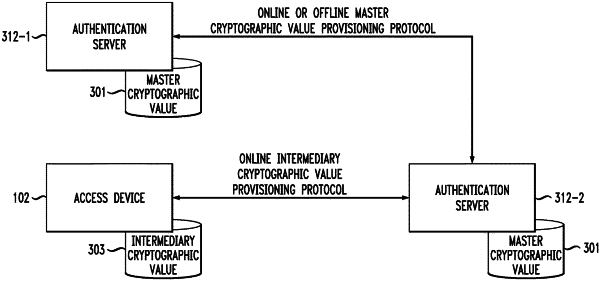
generating, in response to a request from an access device, an intermediary set of cryptographic information from an initial set of cryptographic information, wherein the intermediary set of cryptographic information comprises an intermediary seed comprising a portion of the initial set of cryptographic information and is temporally-limited in accordance with at least a portion of a hierarchy of multiple time-based values, wherein at least one of the multiple time-based values in the hierarchy serves as a predecessor for deriving at least one other of the multiple time-based values in the hierarchy;
modifying the intermediary set of cryptographic information based at least in part on data pertaining to the access device and one or more security parameters, wherein modifying the intermediary set of cryptographic information comprises removing a number of bits of the cryptographic information from the intermediary set, wherein the number of bits removed is adjustable and based at least in part on computational power of the access device; and
transmitting, over a network connection, the modified intermediary set of cryptographic information to the access device and an identification of the number of bits of cryptographic information removed, for use in a subsequent offline authentication request;
wherein the method is performed by an authentication server comprising a processor coupled to a memory.
|