| CPC G06F 11/3636 (2013.01) [G06F 7/588 (2013.01); G06F 11/0772 (2013.01); G06F 11/0778 (2013.01); G06F 11/3664 (2013.01)] | 20 Claims |
|
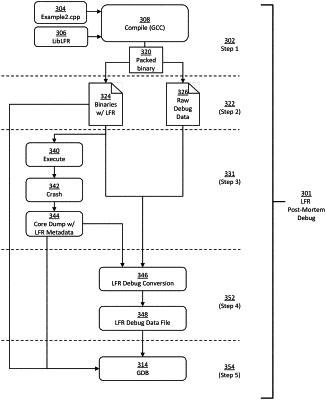
1. A method to debug software that is protected by a cybersecurity technique in which executable code is pseudorandomly reorganized in memory, the method comprising:
loading an executable code component corresponding to a packed binary file into memory, the executable code component including machine code that corresponds to blocks of original source code;
in response to a request for executing the executable code component, generating a pseudorandomly reorganized layout of the machine code corresponding to the blocks of the original source code based on subjecting the executable code component to a transformation defined in a function randomization library corresponding to the blocks of original source code;
in response to a crash event associated with the executing of the pseudorandomly reorganized machine code, receiving a core dump file corresponding to the crash event, the core dump file including information related to memory addresses of the pseudorandomly reorganized layout where portions of the machine code are stored at a time of the crash event;
receiving a debug data file including symbol table information to debug the blocks of the original source code generated prior to the pseudorandomly reorganized layout;
generating an updated debug data file by using the debug data file, wherein the updated debug data file includes symbol table information corresponding to the pseudorandomly reorganized layout based on the information related to the memory addresses of the pseudorandomly reorganized layout at the time of the crash event; and
establishing a post-mortem debugging session by calling a debugger program with the executable code component, the core dump file, and the updated debug data file.
|