| CPC H04W 12/06 (2013.01) [H04L 9/3218 (2013.01); H04L 9/3247 (2013.01); H04L 9/3278 (2013.01); H04W 12/63 (2021.01)] | 18 Claims |
|
1. A method of cryptographic authorization of wireless communications, the method comprising:
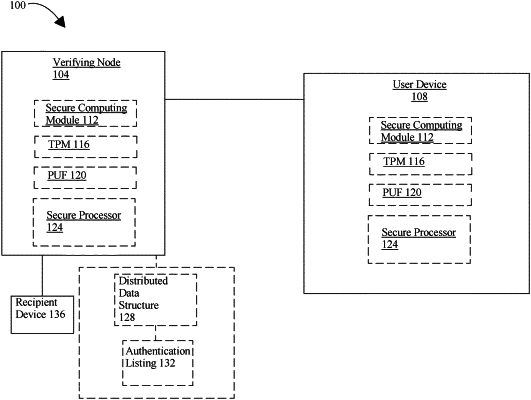
receiving, at a verifying node, a transfer request from a user device to execute an asset transfer transaction;
authenticating, by the verifying node, the transfer request as a function of a biometric authentication;
calculating, by the verifying node, at least a heuristic of trust of the user device by determining a degree of obscurity of the user device;
assigning, by the verifying node, a confidence level to the user device as a function of the biometric authentication and the degree of obscurity of the user device, wherein assigning the confidence level further comprises:
assigning a first threshold confidence level to the user device as a function of at least a first biometric authentication and a second biometric authentication; and
assigning, if the first threshold confidence level is met by the user device, a second threshold confidence level to the user device as a function of the first biometric authentication for a subsequent stage of the asset transfer transaction, wherein the second threshold confidence level is lower than the first threshold confidence level;
generating, by the verifying node, a transfer authorization token, wherein generating the transfer authorization token further comprises:
associating, the transfer request from the user with at least an authorization datum;
digitally signing the authorization datum with a private key, wherein the private key is generated from a physically unclonable function associated with unique physical characteristics of a hardware processor; and
generating the transfer authorization token containing the digitally authorization datum;
providing, by the verifying node, the transfer authorization token to at least one recipient device; and
transferring, from the user device to the at least one recipient, an asset as a function of the transfer authorization token.
|