| CPC H04L 67/14 (2013.01) [H04L 9/06 (2013.01); H04L 9/0891 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 9/32 (2013.01); H04L 67/561 (2022.05)] | 20 Claims |
|
1. An apparatus comprising:
a processor; and
a memory on which is stored machine-readable instructions that when executed by the processor, cause the processor to:
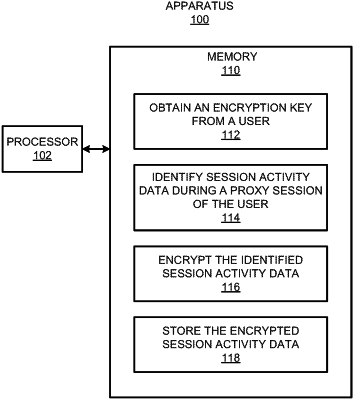
establish, via a proxy service at the apparatus, a proxy session between a client device and a server, the proxy session comprising session data based on communication between the client device and the server;
obtain an encryption key from the client device;
generate session activity data based on the session data during the proxy session, the session activity data including meta data that includes information pertaining to activities performed by the client device during the proxy session between the client device and the server;
identify private data among the meta data, the private data being associated with predetermined fields identified as being private in the session activity data;
encrypt the generated session activity data using the encryption key obtained from the client device; and
store the encrypted session activity data.
|