| CPC H04L 63/164 (2013.01) [H04L 63/029 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method comprising:
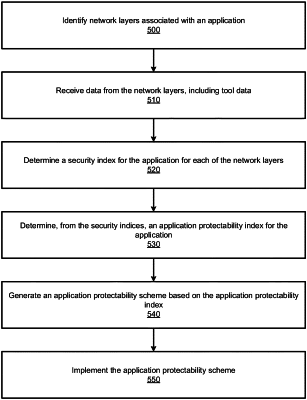
identifying, by a network controller, security layers for implementing an application protectability scheme for an application, wherein incoming network traffic to the application passes through each of the security layers and each of the security layers implements one or more security tools for a specific goal of protecting the application from the incoming network traffic;
determining, for each security layer, a set of security tools that work interdependently as an independent network layer to achieve a specific goal for the security layer, such that a first set of tools for a first security layer applies to incoming traffic to achieve a first goal and a second set of tools for a second security layer applies to the same incoming traffic to achieve a second goal;
determining, by the network controller, a corresponding security index for the application at each of the security layers to yield a plurality of security indexes, each of the plurality of security indexes providing an objective assessment of protectability of the application at a corresponding one of the security layers;
determining, by the network controller, an application protectability index based on the plurality of security indexes;
generating the application protectability scheme for protecting the application based on the application protectability index; and
providing a comparison of security effectiveness between each of the security layers based on the application protectability scheme, wherein the application protectability index determines which security layer provides optimal protection for the application.
|