| CPC G06Q 40/08 (2013.01) [G06Q 40/00 (2013.01); G06Q 40/03 (2023.01)] | 20 Claims |
|
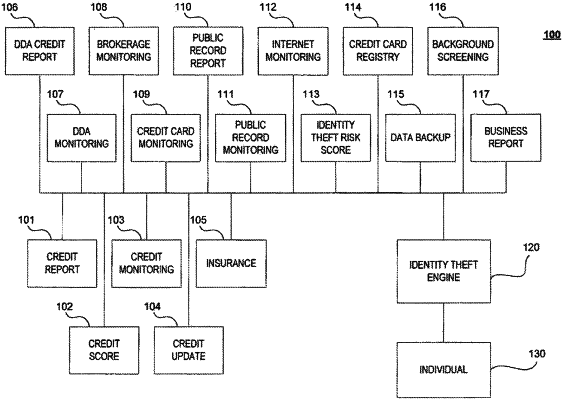
1. A computer-implemented method comprising:
sending, by a first computing system to a second computing system via a graphical user interface displayed by the second computing system:
a list of data providers including one or more financial monitoring data providers, one or more public information data providers, and
a cost amount associated with analyzing information obtained from the financial monitoring data providers from the public information data providers;
receiving, by the first computing system as sent from the second computing system:
a selection of one or more of the financial monitoring data providers and
a selection of one or more of the public information data providers;
receiving, by the first computing system as sent from a first data provider, financial information relating to a user of the second computing system and, as sent from a public information data provider, public information relating to the user of the second computing system;
storing, in the first computer system and over time, the received financial information and received public information;
determining, based on the received public information and the stored public information, at least one of an addition, deletion, or change to the stored public information relating to the user, wherein the determination satisfies a threshold;
sending, from the first computing system based on the determination of the at least one of an addition, deletion, or change, an alert to the second computing system;
preparing, by the first computing system based on the received financial information and the received public information, a report relating to a risk threshold of the user; and
sending the report to the second computing system to enable the user to view, in a unified view provided on a display of the second computing system, the financial information relating to the user and the public information relating to the user.
|