| CPC G06F 21/56 (2013.01) [G06F 21/53 (2013.01); G06N 5/022 (2013.01); G06F 2221/031 (2013.01)] | 21 Claims |
|
1. A system, comprising:
a processor configured to:
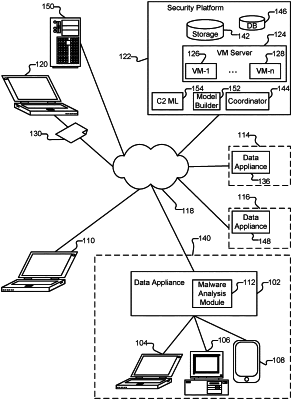
receive a plurality of samples for malware detection analysis using a sandbox;
execute each of the plurality of samples in the sandbox and monitor network traffic during execution of each of the plurality of samples in the sandbox;
detect that one or more of the plurality of samples is malware based on automated analysis of the monitored network traffic using a command and control (C2) machine learning (ML) model if there is not a prior match with an intrusion prevention system (IPS) signature; and
perform an action in response to detecting that the one or more of the plurality of samples is malware based on the automated analysis of the monitored network traffic using the C2 ML model, wherein performing the action in response to detecting that the one or more of the plurality of samples is malware based on the automated analysis of the monitored network traffic using the C2 ML model further comprises the following for each of the detected malware samples:
send the network traffic from the malware sample to a self-learning system for further processing that includes clustering to identify whether the malware sample is associated with an existing C2 malware family and extracting a signature pattern from the network traffic associated with the malware sample, including extracting network traffic session information and payload, to automatically extract a pattern from the network traffic that is common to the existing C2 malware family to generate a new IPS signature; and
a memory coupled to the processor and configured to provide the processor with instructions.
|