| CPC G06F 21/123 (2013.01) [G06F 21/604 (2013.01); H04L 63/101 (2013.01); H04W 12/08 (2013.01)] | 20 Claims |
|
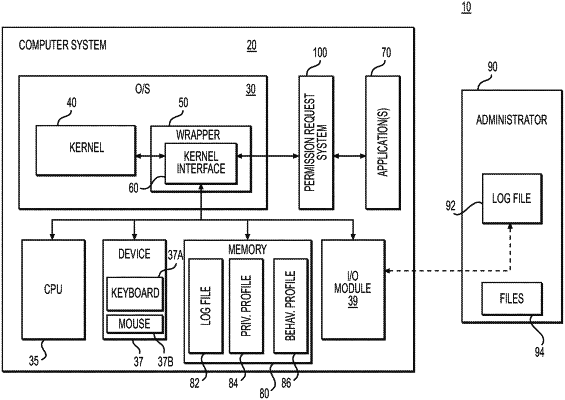
1. A non-transitory, computer-readable storage medium having encoded thereon, machine instructions for establishing and managing computer network access privileges, wherein a processor executes the machine instructions to:
access information related to applications instantiated on a computer system, wherein the information comprises information contained in a privilege profile and in a behavior profile;
identify applications for which neither privilege profiles nor behavior profiles exist;
monitor application instantiations to determine that sufficient information is available to generate a privilege profile and a behavior profile for the application;
create one or more persistent access control lists (ACLs) for the application, and store the persistent ACLs;
receive a system call request from an application;
determine, from a persistent ACL, that the received system call request exists as one of a permanently-allowed system call request and a non-permanently-allowed system call request;
for permanently-allowed system call requests:
determine the system call request pertains to one of a behavior contained in the behavior profile for the application and one of a new behavior for the application,
for a behavior contained in the behavior profile for the application, grant access by the application to an operating system kernel of the computer system, and
for a new behavior, provide a first prompt to a human user to allow or deny the application access to the operating system kernel by way of the system call request; and
for a non-permanently-allowed system call request:
generate a volatile ACL,
provide a second prompt to a human user to allow or deny the application access to the operating system kernel by way of the non-permanently allowed system call request,
add the non-permanently-allowed system call request to the volatile ACL, and
following execution of the application, delete the volatile ACL.
|