| CPC H04L 63/102 (2013.01) [G06F 16/9535 (2019.01); G06F 21/6263 (2013.01)] | 13 Claims |
|
1. A method comprising:
receiving genuine personally identifiable information of a user;
generating artificial personally identifiable information based on the genuine personally identifiable information of the user;
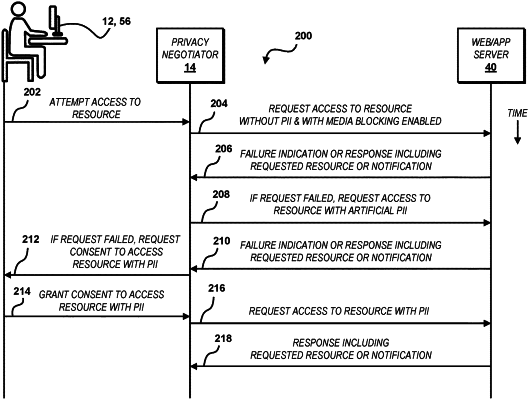
detecting an attempt by the user via a computing device to access a service enabled by a computing system via a network;
transmitting via the network to the computing system a first request to access the service in response to detecting the attempt by the user to access the service, the first request comprising at least one empty personally identifiable data structure;
determining a first failure to access the service responsive to the first request;
transmitting via the network to the computing system a second request to access the service in response to the first failure to access the service, the second request comprising the artificial personally identifiable information; and
receiving access to the service from the computing system for the user.
|