| CPC G06F 21/552 (2013.01) [G06F 9/4498 (2018.02); G06F 16/1734 (2019.01); G06F 16/1748 (2019.01); G06N 20/20 (2019.01)] | 20 Claims |
|
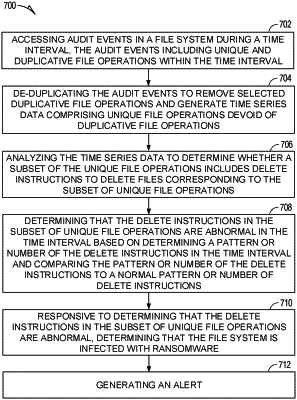
1. A method for real-time detection of a ransomware infection or malicious code in file systems, the method comprising:
accessing audit events in a file system during a time interval, the audit events including unique file operations and duplicative file operations within the time interval;
in a pre-analysis phase, identifying the duplicative file operations based at least in part on the duplicative file operations being successive file operations that maintain corresponding files in file states associated with corresponding prior file operations, and de-duplicating the audit events to remove the duplicative file operations and generate time series data comprising the unique file operations devoid of the duplicative file operations;
in an analysis phase, analyzing the time series data to determine whether a subset of the unique file operations includes delete instructions to delete files corresponding to the subset of the unique file operations;
determining that the delete instructions in the subset of the unique file operations are abnormal in the time interval based at least in part on determining a pattern or number of the delete instructions in the time interval and comparing the pattern or number of the delete instructions to a normal pattern or number of delete instructions;
responsive to determining that the delete instructions in the subset of the unique file operations are abnormal, determining that the file system is infected with ransomware; and
generating an alert.
|