| CPC H04L 63/1441 (2013.01) | 1 Claim |
|
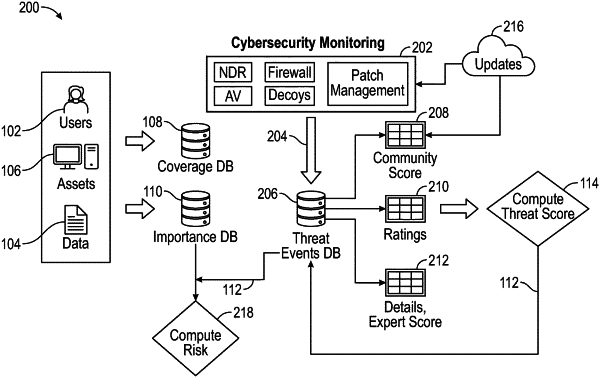
1. A computer-implemented method for computing or modeling the risk of a cyber security breach to an asset, the computer-implemented method comprising executing on a processor the steps of:
gathering coverage information from network sensors, endpoint agents, and decoys related to the asset;
gathering importance information related to the asset, users, and data;
gathering alerts and anomalies from an enterprise;
gathering vulnerability information related to the asset;
computing a threat-score for the asset based on the gathered alerts and anomalies;
gathering connections or coupling information between the users and the assets, between the users and the data, and between the assets and the data, wherein the connections or coupling information between the users and the assets includes at least access or history of usage, the connections or coupling information between the users and the data includes at least data at rest and data in motion, the connections or coupling information between the assets and the data includes at least access rights and data observed in communication;
generating vectors for the assets, the users, and the data based on the gathered connections or coupling information, respectively;
fusing the generated vectors for the assets, the users, and the data to generate a 3-dimensional vector representation of coverage, importance, and threat-score of the assets, the users and the data; and
computing an asset risk score based on the 3-dimensional vector to provide the asset risk score.
|