| CPC H04L 63/105 (2013.01) [H04L 63/104 (2013.01); H04L 63/108 (2013.01)] | 8 Claims |
|
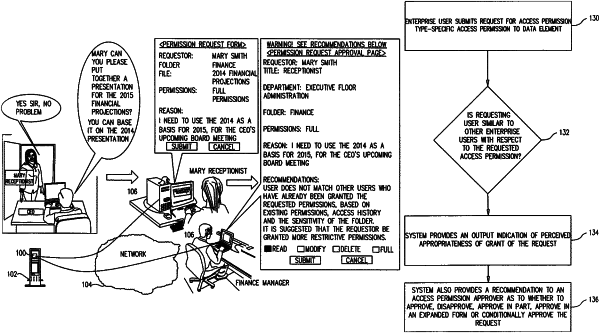
1. A method for processing access permission type-specific access permission requests from enterprise users in an enterprise, the method comprising:
monitoring and recording actual access events of said enterprise users to at least one data element in said enterprise over a learning period;
creating, for each of said enterprise users, an actual access profile based on said recorded actual access events of said enterprise user to said at least one data element;
receiving, at a later time, at least one request for at least one access permission type-specific access permission of at least one enterprise user to at least one data element in said enterprise;
responsive to said receiving said at least one request for said at least one access permission type-specific access permission of said at least one enterprise user to said at least one data element in said enterprise, employing information previously stored in said actual access profiles of ones of said enterprise users having said actual access profiles which are similar to said actual access profile of said at least one enterprise user with respect to at least said access permission type-specific access permission to said data elements and information relating to a sensitivity of said at least one data element, in order to provide an output indication of perceived appropriateness of grant of said request; and
employing said output indication to provide a recommendation to an access permission approver, as to whether to at least one of approve, disapprove, approve in part, approve in an expanded form and conditionally approve
said at least one request,
said recommendation to said access permission approver being based on all of the following conditions:
that the requesting user retains said similarity to said ones of said enterprise users;
that at least one additional access permission approver approves said request; and
that said approval is limited in time.
|