| CPC H04L 63/0815 (2013.01) [H04L 9/321 (2013.01); H04L 63/0421 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A system for securely managing security policy data used to provide users access to third-party applications without revealing credentials to the users, the system comprising:
a permission server, comprising a hardware processor, configured to store permission data comprising a list of third-party applications to which the users are currently permitted access; and
an access management server communicatively coupled to the permission server and a network, the access management server configured to:
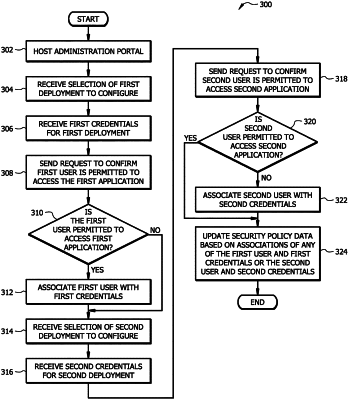
store security policy data, the security policy data comprising, for each user, a list of third-party applications to which the user may request access and corresponding sign-on credentials for accessing each of the third-party applications;
receive a selection of a first deployment to configure, the first deployment corresponding to a first third-party application and a first network address for a first sign-on page of the first third-party application;
receive first sign-on credentials for the first deployment, wherein the first sign-on credentials provide access to the first third-party application via the first sign-on page;
receive a selection of a second deployment to configure, the second deployment corresponding to a second third-party application and a second network address for a second sign-on page of the second third-party application;
receive second sign-on credentials for the second deployment, wherein the second sign-on credentials provide access to the second third-party application via the second sign-on page;
in response to an attempt to associate the first sign-on credentials with a first user, send a first request to the permission server to confirm that the first user is permitted access to the first third-party application;
receive a first response to the first request, wherein the first response comprises a confirmation or denial of permission to access the first third-party application by the first user;
in response to the first response comprising a confirmation of permission to access the first third-party application by the first user, associate the first user with the first sign-on credentials;
in response to an attempt to associate the second sign-on credentials with a second user, send a second request to the permission server to confirm that the second user is permitted access to the second third-party application;
receive a second response to the second request from the permission server, wherein the second response comprises a confirmation or denial of permission to access the second third-party application by the second user;
in response to the second response comprising a confirmation of permission to access the second third-party application by the second user, associate the second user with the second sign-on credentials; and
automatically update the security policy data, based on the association of the first sign-on credentials with the first user and the association of the second sign-on credentials with the second user, such that the security policy data comprises:
a first entry for the first deployment, the first entry comprising an identifier of the first user, the first sign-on credentials, and the first network address; and
a second entry for the second deployment, the second entry comprising an identifier of the second user, the second sign-on credentials, and the second network address.
|