| CPC H04L 9/3268 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0825 (2013.01); H04L 9/3297 (2013.01)] | 20 Claims |
|
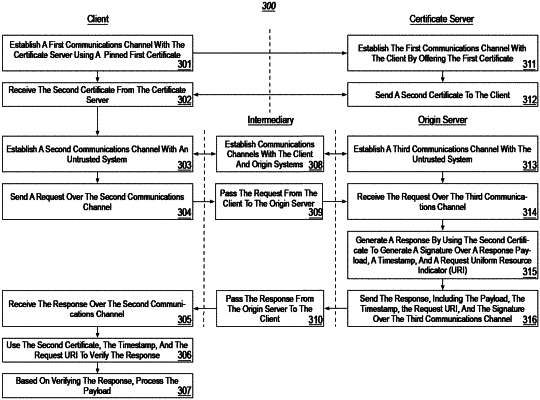
1. A method, implemented at a computer system that includes at least one processor, for achieving certificate pinning security when obtaining data through a reduced trust network, the method comprising:
receiving, over a first secured communications channel, an identity of a second digital certificate, the second digital certificate to be used to verify integrity and authenticity of content received over a second communications channel established with an untrusted second remote computer system, the first secured communications channel established based at least upon a first digital certificate associated with the first secured communications channel being certified by a pinned certificate;
sending a request over the second communications channel, the request including a request Uniform Resource Identifier (URI);
based on sending the request, receiving a response from the untrusted second remote computer system over the second communications channel, the response comprising a payload, a timestamp, a URI portion, and a signature over the payload, the timestamp, the URI portion;
verifying integrity and authenticity of the response, including:
verifying that the timestamp is valid;
verifying that the URI portion corresponds to the request URI; and
using the second digital certificate and the signature, verifying that the response is authentic; and
based on verifying the integrity and the authenticity of the response, processing the payload.
|