| CPC H04L 9/32 (2013.01) [B60W 60/001 (2020.02); H04L 9/0819 (2013.01)] | 20 Claims |
|
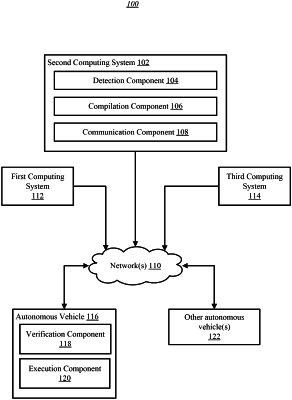
1. A system for managing a compromised autonomous vehicle server, the system comprising:
one or more processors; and
one or more memories storing instructions that, when executed by the one or more processors, cause the system to perform:
obtaining an indication of a first server configured to control an autonomous vehicle being compromised, the autonomous vehicle having previously been provisioned with a first public key, the first public key being paired with a first private key;
compiling command information, the command information including a command for the autonomous vehicle and a digital certificate of a second server configured to control the autonomous vehicle in an event of the first server being compromised, the digital certificate including a second public key and being signed with the first private key, the command being signed with a second private key associated with the second server, the second private key being paired with the second public key; and
wherein the autonomous vehicle is part of a fleet of autonomous vehicles such that operations of the system are performed for an individual autonomous vehicle of the fleet of autonomous vehicles, and the command information facilitates:
verifying, at the autonomous vehicle, the digital certificate using the first public key;
in response to the digital certificate being verified, extracting, from the digital certificate, the second public key;
verifying, at the autonomous vehicle, the command using the second public key; and
in response to the command being verified, executing, at the autonomous vehicle, the command.
|