| CPC H04L 9/003 (2013.01) [H04L 9/0618 (2013.01); H04L 9/0844 (2013.01); H04L 9/3242 (2013.01)] | 20 Claims |
|
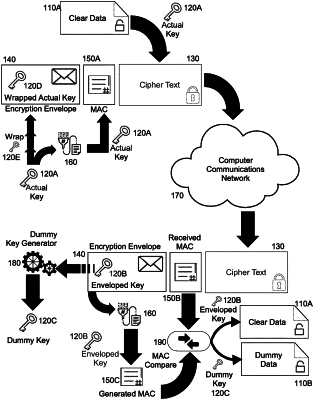
1. A computer-implemented method for side-channel attack mitigation in streaming encryption, the method when executed by data processing hardware causes the data processing hardware to perform operations comprising:
reading an input stream into a decryption process;
extracting from the input stream:
an encryption envelope having a wrapped key;
a cipher text; and
a first message authentication code (MAC);
generating a second MAC using the wrapped key of the encryption envelope; and
performing decryption of the cipher text in constant time by:
determining whether the encryption envelope is authentic by comparing the first MAC extracted from the encryption envelope and the second MAC generated using the wrapped key;
when the encryption envelope is authentic, generating an authenticated decryption of the cipher text using the wrapped key of the encryption envelope; and
wherein performing decryption of the cipher text in constant time indicates whether the wrapped key is an actual key that generated the cipher text of the encryption envelope.
|