| CPC G06Q 10/067 (2013.01) [H04L 47/762 (2013.01); H04L 47/781 (2013.01); H04L 47/822 (2013.01); H04L 65/65 (2022.05); H04L 65/80 (2013.01)] | 18 Claims |
|
1. A computing platform, comprising:
at least one processor;
a communication interface communicatively coupled to the at least one processor; and
memory storing computer-readable instructions that, when executed by the at least one processor, cause the computing platform to:
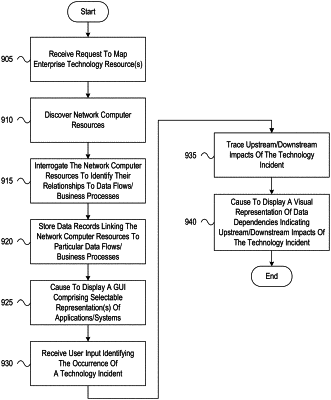
generate a business capability model, wherein generating the business capability model comprises:
discovering network computer resources; and
interrogating the network computer resources to identify relationships between the network computer resources and data flows associated with one or more business processes;
cause a graphical user interface comprising one or more selectable graphical representations of one or more applications associated with one or more enterprise technology resources to be displayed on a display device of a user computing device;
receive, via the communication interface, a first user input identifying an occurrence of a technology incident by selecting one of the graphical representations of the one or more applications, the occurrence of the technology incident including one of: a technology fault or a cyber attack;
in response to receiving the first user input, use the business capability model to automatically trace an impact of the technology incident by generating a visible path across network computer resources affected by the identified technology incident without a human manually tracing the impact of the technology incident;
cause a visual representation of data dependencies indicating the impact of the technology incident to be displayed on the display device of the user computing device;
receive a second user input simulating an addition of one or more applications by interacting with the graphical user interface;
in response to receiving the second user input, use the business capability model to automatically trace an impact of adding the one or more applications by generating a visible path across network computer resources affected by the addition of the one or more applications without a human manually tracing the impact of the addition; and
cause a second visual representation of data dependencies indicating the impact of adding the one or more applications to be displayed on the display device of the user computing device.
|