| CPC G06F 21/79 (2013.01) [G06F 21/602 (2013.01); G06F 21/805 (2013.01); G06F 2221/0751 (2013.01)] | 19 Claims |
|
1. A system comprising:
a memory device; and
a processing device coupled to the memory device, the processing device configured to perform operations comprising:
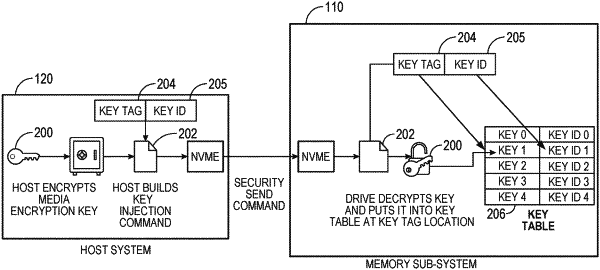
receiving a first command to perform a first data operation at the memory device, the first command comprising a first encryption key tag;
accessing a first key table from local memory, the first key table comprising a first set of key entries corresponding to a first set of encryption keys;
determining whether the first key table includes an entry corresponding to the first encryption key tag;
based on determining the first key table does not include an entry corresponding to the first encryption key tag, accessing, from random access memory (RAM), a second key table comprising a second set of key entries corresponding to a second set of encryption keys;
identifying, from the second set of key entries, a first key entry corresponding to the first encryption key tag, the first key entry comprising a first encryption key corresponding to the first encryption key tag;
processing the first command using the first encryption key;
receiving a second command to perform a second data operation at the memory device, the second command comprising a second encryption key tag;
determining the first key table does not include a key entry corresponding to the second encryption key tag;
identifying a second key entry from the second key table that corresponds to the second encryption key tag; and
replacing an existing key entry in the first key table with the second key entry from the second key table that corresponds to the second encryption key tag.
|