| CPC G06F 21/6245 (2013.01) | 20 Claims |
|
1. A system to improve power management in a computer network, comprising:
a memory;
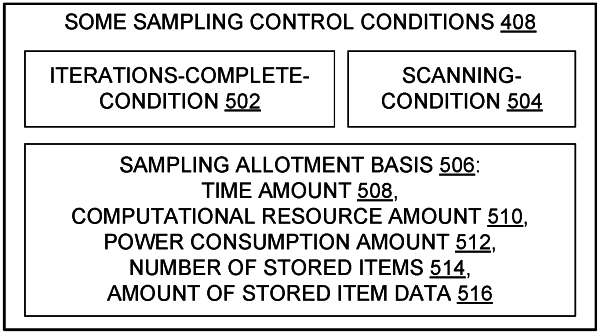
a processor which is in operable communication with the memory, the processor configured to configure the memory with instructions and data and perform steps which include providing data security classification statistics by (a) getting an iterations-complete-condition, and (b) iteratively repeating a data sampling sequence until the iterations-complete-condition is met, wherein the data sampling sequence of a current iteration includes (b1) selecting a current iteration scan-set of stored items from a group of stored items in the computer network, the selecting based at least partially on a current iteration power consumption budget representing an amount of electric power consumption in the computer network, (b2) when a scanning-condition is met then in response scanning data of the current iteration scan-set for sensitive data which meets a predefined sensitivity criterion which defines a sensitivity type, (b3) when scanned data of a particular stored item of the current iteration scan-set includes sensitive data which meets the predefined sensitivity criterion, then in response labeling the particular stored item with a predefined sensitivity label which corresponds to the predefined sensitivity criterion, and when the scanned data of a particular stored item does not include data which meets the predefined sensitivity criterion, then in response avoiding labeling the particular stored item with the predefined sensitivity label, (b4) updating a data security classification statistical measure in response to the labeling or the avoiding labeling, (b5) calculating a next iteration power consumption budget which is based at least partially on the current iteration power consumption budget and the data security classification statistical measure, and (b6) when the iterations-complete-condition is not met, then in response using the next iteration power consumption budget as the current iteration power consumption budget of a next iteration of the data sampling sequence;
whereby the system manages power consumption in the computer network during data security classification by selectively limiting which stored items are scanned for data that meets the predefined sensitivity criterion instead of scanning all stored items.
|