| CPC G06F 21/577 (2013.01) [G06F 21/554 (2013.01); H04L 63/1433 (2013.01)] | 24 Claims |
|
1. A method, comprising:
performing the following within a code vendor environment:
developing an executable target code,
then associating the executable target code with one or more threat indicators and/or one or more behaviors, and
then creating a data set including the executable target code and the one or more associated threat indicators and/or behaviors;
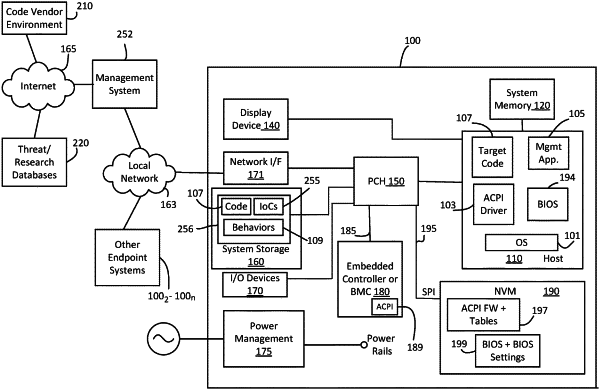
then releasing the data set from the code vendor environment by providing the data set including the executable target code and the one or more associated threat indicators and/or behaviors across a network from a first information handling system of the code vendor environment to at least one other different information handling system that comprises an endpoint information handling system or to a second information handling system that is different from each of the first information handling system and the endpoint information handling system, and that is coupled to and managing the endpoint information handling system;
then receiving the data set including the executable target code from across the network, and installing the executable target code from the data set onto the endpoint information handling system;
then executing the installed executable target code from the data set on a programmable integrated circuit of the endpoint information handling system while using the associated threat indicators and/or behaviors to detect the presence of a threat associated with the executable target code on the endpoint information handling system without taking any further action to associate the executable target code with the one or more threat indicators and/or one or more behaviors; and
then taking at least one automatic action and/or providing at least one alert only upon detection of the presence of the threat associated with the executable target code on the endpoint information handling system;
where the one or more behaviors comprise at least one of expected behaviors associated with the executable target code or unexpected behaviors associated with the executable target code.
|