| CPC G06F 21/33 (2013.01) [G06F 21/36 (2013.01); G06V 10/443 (2022.01); H04L 12/1822 (2013.01)] | 20 Claims |
|
1. A method of authenticating an identity of an individual, the method comprising:
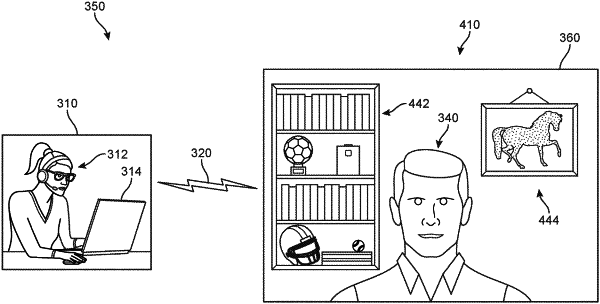
obtaining first image data at a first time from a first computing device associated with a first user, the first image data including a virtual representation of a real-world object that is located in proximity to the first user;
executing an object recognition protocol to detect one or more objects in a background of the first image data, the one or more objects including the real-world object;
receiving, from the first user, a selection of the real-world object;
tagging, in response to the selection, the real-world object in the first image data as a verification object token;
receiving, at a second time after the first time, a request for access by a first person to a secured resource associated with the first user;
obtaining, in response to the request for access, second image data that includes a virtual representation of the real-world object;
executing the object recognition protocol to detect one or more objects in a background of the second image data, the one or more objects including the real-world object;
tagging the real-world object in the second image data as an object token;
determining if the object token and the verification object token sufficiently match;
determining, in response to the object token matching the verification object token, the first person is the first user; and
thereby authenticating the first person for access to the secured resource.
|