| CPC H04W 12/06 (2013.01) [H04W 12/041 (2021.01); H04W 12/0431 (2021.01); H04W 12/106 (2021.01); H04W 84/042 (2013.01); H04W 84/12 (2013.01)] | 20 Claims |
|
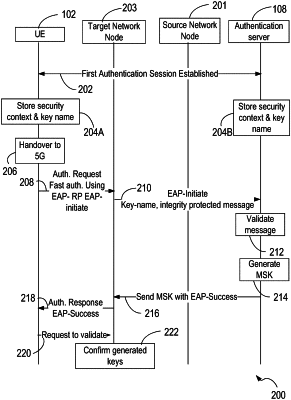
1. A computer-implemented method comprising:
receiving, at a target network node associated with a target network and from a User Equipment (UE), a re-authentication initiate request comprising both (1) a key name associated with a previously-authenticated session of the UE at a source network and (2) an integrity protected message generated by the UE using a key identified by the key name, the target network comprising one of a 5G network or a Wi-Fi network and the source network comprising a different one of the 5G network or the Wi-Fi network;
sending the re-authentication initiate request with the key name to an authentication server associated with the target network and the source network, wherein the authentication server stores the key in connection with the previously-authenticated session of the UE at the source network and prior to receiving the re-authentication initiate request and wherein the authentication server validates the integrity protected message and generates a re-authentication master session key (MSK);
receiving, from the authentication server, the re-authentication MSK associated with the previously-authenticated session of the UE authenticated for the source network based on the key name; and
authenticating a session between the UE and the target network based on the re-authentication MSK and a session key generated by the UE and associated with the key name and the integrity protected message.
|