| CPC H04L 63/1433 (2013.01) [H04L 9/3247 (2013.01); H04L 9/3268 (2013.01); H04L 63/061 (2013.01); H04L 63/12 (2013.01); H04L 63/166 (2013.01)] | 22 Claims |
|
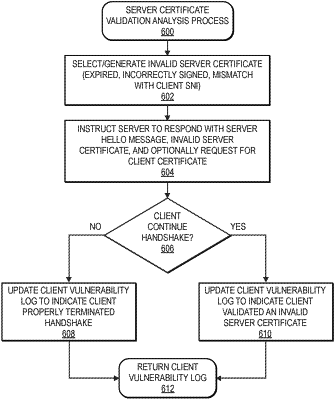
1. A computer-implemented method to determine one or more device vulnerabilities of a client device, comprising:
receiving, at a vulnerability detector, a client hello message sent from the client device to a server, the vulnerability detector positioned to observe messages sent between the client device and the server as part of a Transport Layer Security (“TLS”) handshake;
determining that a server certificate sent from the server to the client device in response to the client hello message is at least one of incorrectly signed or expired;
receiving, at the vulnerability detector, a client key exchange message sent from the client device to the server;
determining, with the vulnerability detector and based on receipt of the client key exchange message and determination that the server certificate is at least one of incorrectly signed or expired, that the client device validated the server based on an invalid server certificate;
generating, based at least in part on the processing of the client hello message and in response to determining that the client key exchange message was received and that the server certificate is at least one of incorrectly signed or expired, a client device vulnerability log indicating that the client device validated the server based on the invalid server certificate; and
providing the client device vulnerability log to cause a vulnerability of the client device to be resolved.
|