| CPC H04L 63/1408 (2013.01) [H04L 63/0254 (2013.01); H04L 63/168 (2013.01); H04L 63/0245 (2013.01); H04L 63/1416 (2013.01); H04L 67/104 (2013.01)] | 20 Claims |
|
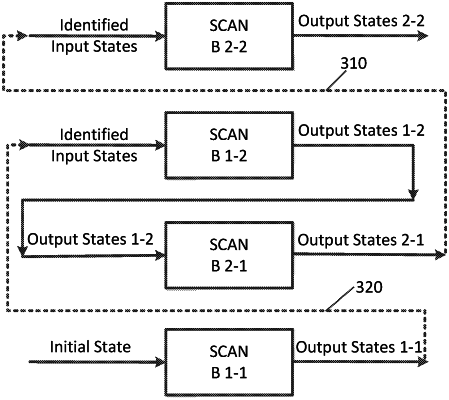
1. A method for scanning computer data, the method comprising:
scanning a first out-of-order portion of a dataset from an input state associated with malware, wherein the first out-of-order portion is sent to a destination after the scanning;
generating a pattern that identifies the malware as a result of the scanning the first out-of-order portion;
generating an output state by scanning a second out-of-order portion of the dataset that immediately precedes the first out-of-order portion of the dataset;
identifying that the dataset includes a set of malware based on matching of the input and output state; and
blocking the second out-of-order portion of the dataset from being sent to the destination based on the identification that the dataset includes the set of malware.
|