| CPC H04L 63/029 (2013.01) [G06F 9/45558 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
1. A computing system for providing an operations and maintenance subsystem for supporting secure classified remote access as a service virtual desktop infrastructure, comprising:
one or more processors,
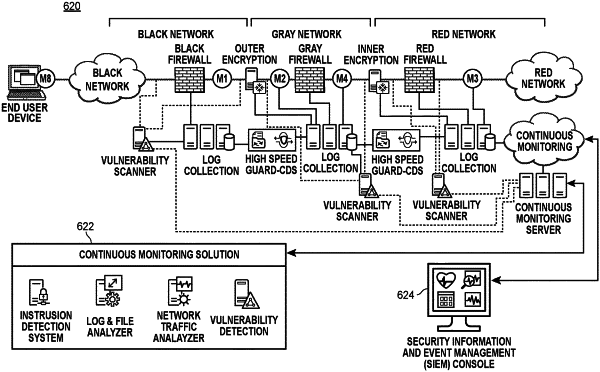
one or more network interface controllers configured to communicate via a black network, a gray network and a red network;
a secure classified remote access as a service virtual desktop infrastructure managed services operations team application, wherein the secure classified remote access as service virtual desktop infrastructure managed services operations team application includes computer-executable instructions for performing systems administration, network operations, security operation and services desk operations; and
an information technology service management application,
wherein the information technology service management application includes computer-executable instructions for performing general management, service management and technical management;
wherein the information technology service management application is accessible to the secure classified remote access as a service virtual desktop infrastructure managed services operations team application via the one or more network interface controllers; and
wherein the instructions of the secure classified remote access as a service virtual desktop infrastructure managed services operations team application, when executed by the one or more processors, are configured to cause the system to:
perform systematic monitoring operations and maintain a virtual hosting environment;
perform a network vulnerability analysis;
remediate a finding of the network vulnerability analysis by hardening at least one of network port access, iOS upgrades, access control lists, audit logging, physical access or administrator access control; and
notify a user of a potential issue related to the network vulnerability analysis before an incident occurs.
|