| CPC G06F 21/6227 (2013.01) [G06F 21/604 (2013.01); G06F 21/78 (2013.01)] | 20 Claims |
|
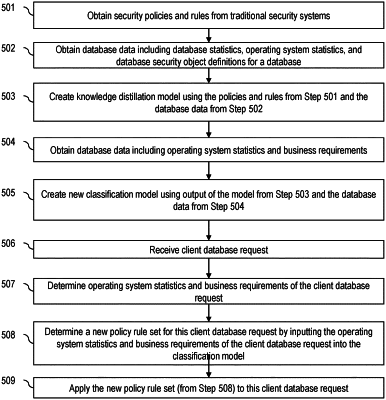
1. A method, comprising:
obtaining, by a database server, security policies associated with a database hosted by the database server;
obtaining, by the database server, first database data associated with the database, wherein the first database data comprises database security object definitions of the database;
creating, by the database server, a knowledge distillation model using the security policies and the first database data;
obtaining, by the database server, second database data associated with the database, wherein the second database data comprises business requirements data;
creating, by the database server, a classification model using the second database data and an output of the knowledge distillation model;
receiving, by the database server, a client database request to the database;
determining, by the database server, a new security policy rule set using the classification model; and
applying, by the database server, the new security policy rule set to the client database request.
|