| CPC H04W 12/12 (2013.01) [H04L 63/14 (2013.01); H04L 63/1466 (2013.01); H04M 1/67 (2013.01); H04M 1/72463 (2021.01)] | 20 Claims |
|
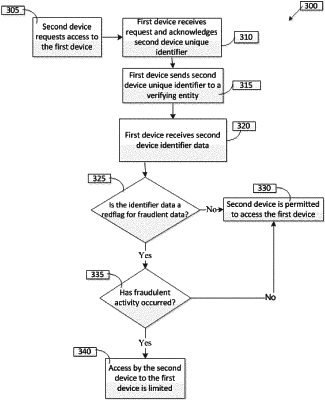
1. A method, comprising:
receiving, by a first network device comprising a processor, identity data associated with a second network device utilizing a telephone number of a telecommunications network, an IP address assigned to the second wireless network device, or a piece of profile data associated with the second wireless network device;
based on the identity data, determining, by the first network device, that a fraudulent action associated with the second network device has occurred;
in response to determining that the fraudulent action has occurred, preventing, by the first network device, the second network device from utilizing a mobile application associated with the first network device;
wherein the determination that the fraudulent action has occurred is based on a determination that a text string received from the second network device is incoherent.
|