| CPC H04W 12/02 (2013.01) [H04W 8/22 (2013.01); H04W 64/003 (2013.01)] | 20 Claims |
|
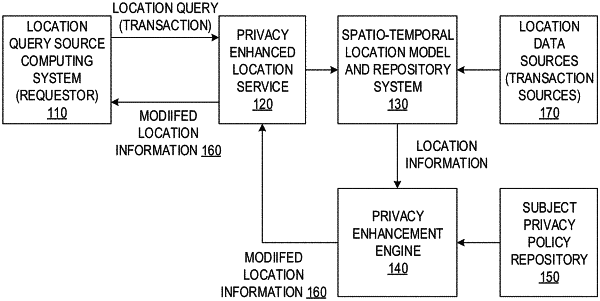
1. A method, in a data processing system comprising a processor and a memory, the memory comprising instructions executed by the processor to configure the processor to implement a privacy enhanced location service, the method comprising:
receiving, by the privacy enhanced location service, from a requestor computing device, a location query requesting location information for a subject;
retrieving, by the privacy enhanced location service, a selected subject privacy policy data structure, selected from a set of subject privacy policy data structures corresponding to the subject identified in the location query;
applying, by the privacy enhanced location service, the selected subject privacy policy data structure to location information associated with the subject to generate modified location information having a granularity of location information specified in the selected subject privacy policy data structure; and
transmitting, by the privacy enhanced location service, the modified location information to the requestor computing device, wherein the selected subject privacy policy data structure comprises at least one negotiation limit criterion specifying a limit to increasing a specificity of the location information in response to an automated negotiation operation between the data processing system and the requestor computing device, and wherein applying the selected subject privacy policy data structure comprises executing an automated negotiation operation between the data processing system and the requestor computing device based on the at least one negotiation limit criterion.
|