| CPC H04M 3/436 (2013.01) [H04L 9/06 (2013.01); H04W 12/12 (2013.01); H04W 12/72 (2021.01); H04L 9/50 (2022.05); H04M 2203/6027 (2013.01)] | 21 Claims |
|
1. A method for determining and blocking robocall communications comprising the steps of:
(A) providing a plurality of user accounts managed by at least one remote server, wherein each of the plurality of user accounts is associated with a corresponding personal computing (PC) device;
(B) receiving a call for connection from a random caller for communication with the corresponding PC device of a specific user account through the remote server;
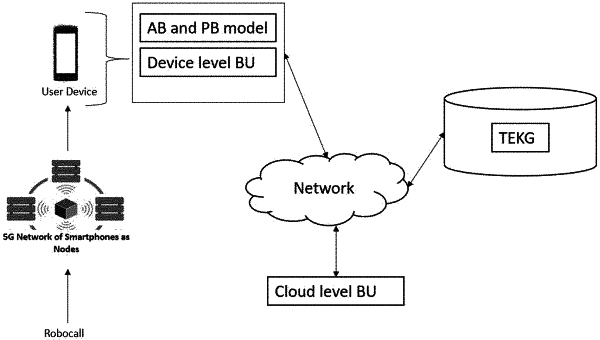
(C) determining if the connection request is a robocall with a call blocking mechanism through the remote server, wherein the call blocking mechanism comprises a blockchain unit (BU) and a telecommunication expert knowledge graph (TEKG) for call analysis and handling;
(D) blocking the call with the corresponding PC device of the specific user account, if the call is determined to be a robocall with a statistical significance of a predetermined confidence; and
(E) updating the blockchain record of the call using the BU through the remote server, wherein the detailed information of call analysis and handling is used to update the TEKG and shared with all user accounts;
determining if the call is from a subscriber using an active blocking (AB) module of the call blocking mechanism with the corresponding PC device of the specific user account in step (C);
analyzing the call using a swarm intelligence (SI), machine learning (ML), and/or artificial intelligence (AI) application of the AB module if the call is not from a subscriber;
determining if the call from the nonsubscriber violates a policy of a plurality of SDDRC (scam/deepfake/disinformation call) policies established in TEKG according to the statistical significance of the predetermined confidence; and
sending the policy-violating robocall from the nonsubscriber to step (D) for blocking.
|