| CPC H04L 63/1425 (2013.01) [H04L 63/1416 (2013.01); H04L 63/1441 (2013.01); H04L 63/1458 (2013.01); H04L 63/1483 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A system comprising:
a processor; and
a first security policy engine (SPE) configured to execute on the processor to:
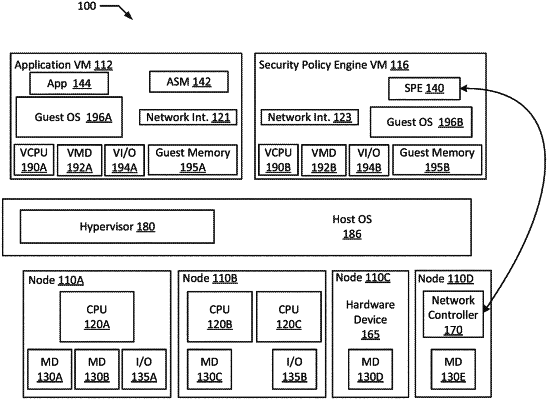
communicate with a plurality of application security modules including a first application security module (ASM), wherein the first ASM is configured to detect abnormalities for a first application, identify a source and a mode of a first abnormality, and determine that the first abnormality individually does not meet a first threshold for taking an action, wherein each of the abnormalities is identifiable with at least a respective threshold of a respective mode;
receive, from the first ASM, the source and the mode;
correlate a plurality of abnormalities including the first abnormality; and
adjust a second threshold used by a second ASM associated with a different second application for detecting the mode, such that the second ASM is configured to detect a second abnormality with the mode and prevent the second application from being affected by the second abnormality.
|